Cyberattacks have increasingly prevalent and sophisticated, posing a significant threat to businesses of all sizes. These attacks can lead to severe consequences, such as financial losses, reputational damage, and operational disruptions. In this blog post, we will proactive cybersecurity measures that businesses can implement to protect themselves from cyber threats.
What is Cyberattacks?
Cyberattacks are malicious manoeuvres targeting computer systems to steal, disrupt, alter, or destroy data, infrastructure, or devices. These attacks, launched by individuals or groups called threat actors, use tactics like malware, phishing, and password theft to gain unauthorized access, causing financial losses, operational disruption, and privacy breaches for individuals and organizations alike.
Securing Your Networks and Systems
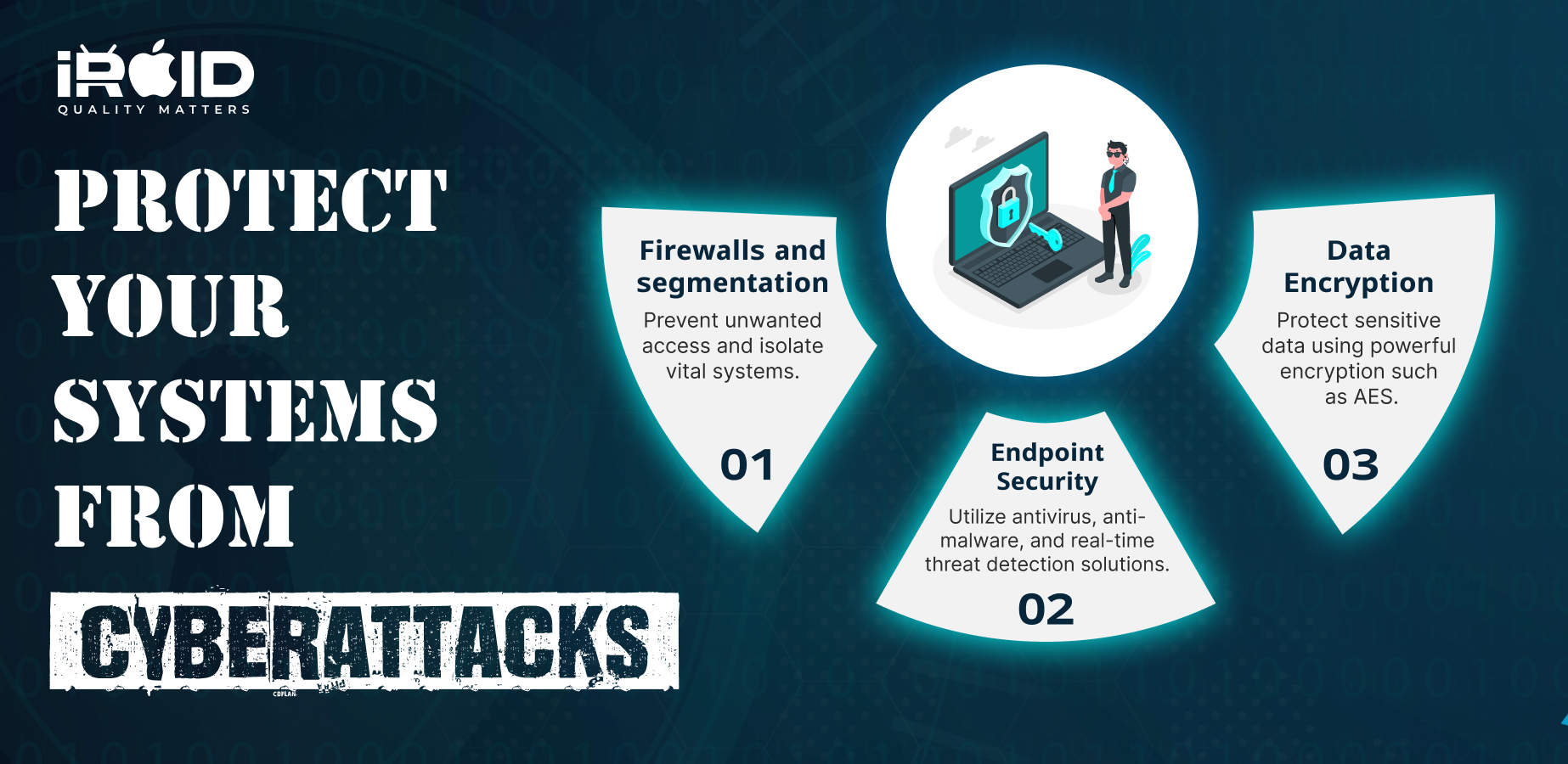
Firewalls and Network Segmentation
Firewalls play a crucial role in controlling network traffic and preventing unauthorized access. By establishing a barrier between internal and external networks, firewalls deter potential attackers. Additionally, network segmentation is key to minimizing the impact of an attack. By dividing the network into isolated segments, critical systems can be protected, limiting the attacker's reach.
Endpoint Security
To safeguard against cyberattacks, it is vital to prioritize endpoint security. Ensure antivirus and anti-malware software is installed on all devices, including computers, servers, and mobile devices. This software scans for and eliminates malicious programs before they can cause harm. Consider implementing endpoint detection and response (EDR) solutions for real-time threat detection and incident response. These solutions provide additional layers of defence, boosting your organization's cybersecurity posture.
Data Encryption
Data encryption is a crucial component of protecting sensitive information. It ensures that data remains secure both at rest and in transit. Implementing robust encryption methods, such as Advanced Encryption Standard (AES), helps safeguard data from unauthorized access. Equally important are strong encryption keys, which add an extra layer of protection against potential breaches.
Employee Security Awareness and Training
Phishing and Social Engineering
Employees play a vital role in maintaining a secure business environment. Educate them about the dangers of phishing emails and social engineering scams. Train them to identify suspicious emails and links, teaching them tactics used by attackers, such as email spoofing and deceptive URLs. By fostering a strong security awareness culture, businesses can mitigate risks associated with phishing attacks.
Password Security
Passwords act as the first line of defence against unauthorized access. Implement strong password policies that require complex passwords and regular changes. Encourage employees to choose unique passwords, avoiding common phrases or easily guessable information. Consider implementing multi-factor authentication (MFA) for an added layer of security. MFA provides an extra level of verification, making it more challenging for attackers to compromise accounts.
General Security Awareness
Cybersecurity best practices should be ingrained in the minds of all employees. Train them on fundamental security measures, such as not downloading files from untrusted sources and reporting suspicious activity. Promote responsible online behaviour and highlight the importance of practising caution when sharing sensitive information. By empowering employees with knowledge, businesses can create a strong human firewall against cyber threats.
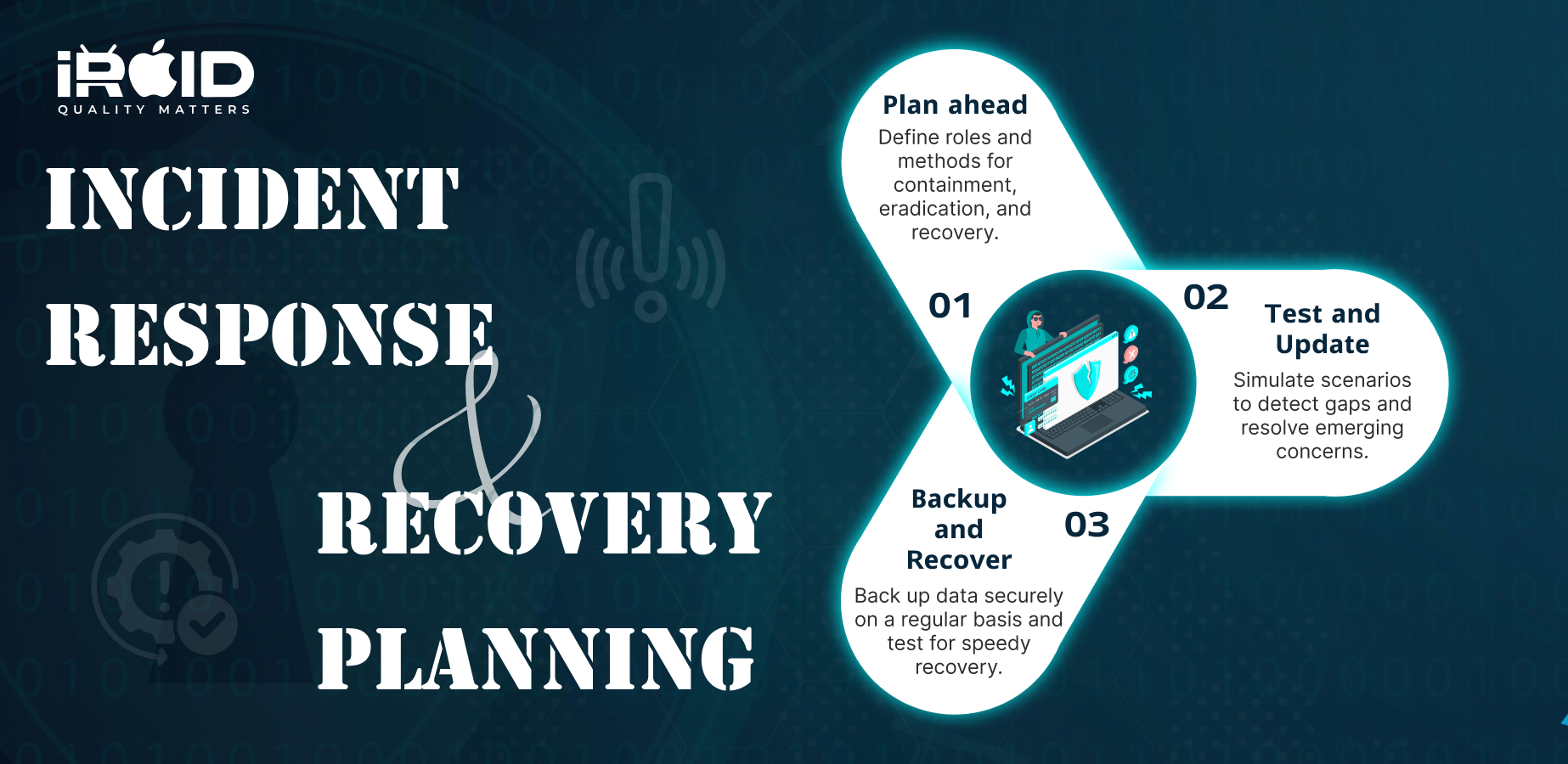
Incident Response and Recovery Planning
Having a Plan
Preparing for a potential cyberattack is essential. Businesses must have a comprehensive incident response plan in place, outlining the steps to take in case of an attack. This plan should cover containment, eradication, and recovery strategies. Assign roles and responsibilities to ensure a swift and organized response that minimizes the impact of an incident.
Regular Testing and Updating
An incident response plan is only effective if it is regularly tested and updated. Conduct mock exercises to simulate real-world scenarios, identifying any weaknesses or gaps in the plan. Test the response team's ability to execute the plan and refine it based on the insights gained. Additionally, stay updated on the latest threats and vulnerabilities to ensure your plan reflects the changing landscape of cybersecurity.
Backup and Recovery
Regularly backing up your data is critical for effective recovery in the event of an attack. Maintain secure and encrypted backups that are stored separately from your primary systems. Test these backups regularly to ensure their accessibility and integrity. By having reliable backups, businesses can quickly restore their operations, minimizing downtime and potential financial losses.
Conclusion
In today's digital landscape, cybersecurity isn't optional, it's an urgent priority. Every organization will face a cyberattack, it's just a matter of when. But proactive measures like securing networks, training employees, and having a solid incident response plan can shield your valuable assets. Stay informed about evolving threats and don't hesitate to seek expert help from iRoid Solutions, industry resources, and government agencies promoting cyber best practices. Protect your business, protect your future – stay cyber-safe. Contact us today and let's create a secure digital world together!
Blog Related FAQs:
A cyberattack is a malicious attempt to disrupt, steal, or damage data, systems, or infrastructure. For businesses, it can result in financial losses, operational disruptions, and reputational damage.
Use firewalls, enable network segmentation, and implement endpoint security solutions like antivirus and EDR (Endpoint Detection and Response) software to safeguard your systems.
Data encryption converts sensitive information into unreadable code, protecting it from unauthorized access. It ensures your data remains secure during storage and transmission.
Contain the breach, identify the attack’s source, restore operations using backups, and update your security measures to prevent future attacks. Seek professional guidance if needed.
iRoid Solutions offers tailored cybersecurity services, including network security, employee training, and incident response planning, to help safeguard your business against evolving threats.
Recent Blog Posts
Get in Touch With Us
If you are looking for a solid partner for your projects, send us an email. We'd love to talk to you!